Introduction
This paper is published in CCS 2017. In the paper, the paper proposes a dynamic analysis (Newton) to find function gadgets even in the presence of state-of-the-art code reuse defenses. In the end of this paper, the author gives an in-depth analysis on nginx and present attacks under the restriction of CPI and Context-sensitive CFI.
Overview of Newton
Newton applies a uniform and blackbox strategy to dynamically retrieve gadgets as a set of attacker-controllable forward CFG edges. Newton accepts a number of user-defined constraints (given in next section) that limit the analysis to only gadgets allowed by the given modeled defense.
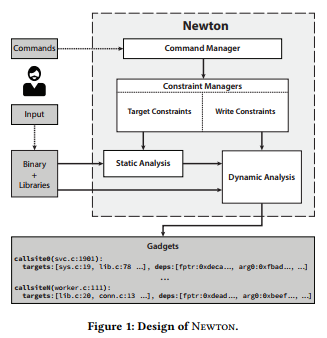
Write Constraint Manager: The write constraint manager accepts user-defined constraints, describing the memory regions the attacker is allowed to overwrite under the modeled defense. Then, using constraint-driven dynamic taint analysis, it pinpoints callsites and arguments which can still be controlled by the attacker.
Target Constraint Manager: The target constraint manager models constraints imposed by code reuse defenses. It uses static and dynamic analysis to extract callsite and callee information, which it then uses to impose the user-defined constraint policy. During dynamic analysis, the author defines a live code page as a memory page pointed to by a live code pointer, i.e., a code pointer stored in live data memory that can be leaked and overwritten.
Mapping Defenses in Newton
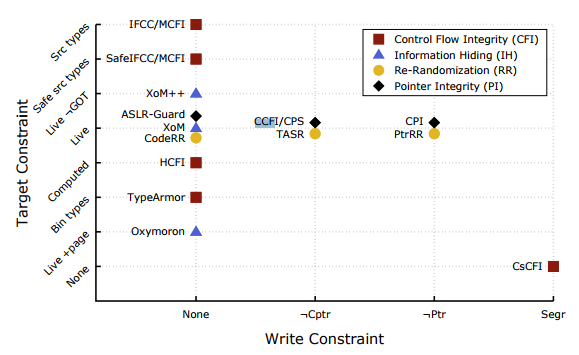
In the paper, the author gives an overview of state-of-the-art code-reuse defenses at present: (1)Control-Flow integrity, (2)Information hiding, (3) Re-randomization, (4)Pointer Inegrity. Base on the write-constraint and target constraint, the paper gives a table mapping the constraints to different defenses.

Write constraint:
Segr: Limits writes to the segregated state specified by the attacker
CPtr: Forbids writes to memory locations containing code pointers.
Ptr: Forbids writes to memory locations containing either code or data pointers.
Target constraint:
Live: Limits the set of valid targets to live code pointers
Live+page: Limits the set of valid (i.e., attacker-leaked) targets to pages pointed to by live code pointers.
Live GOT: Live code pointers in the GOT are no longer valid
Computed: the set of valid targets for each call site is determined by the set of code pointers that have been computed during the execution.
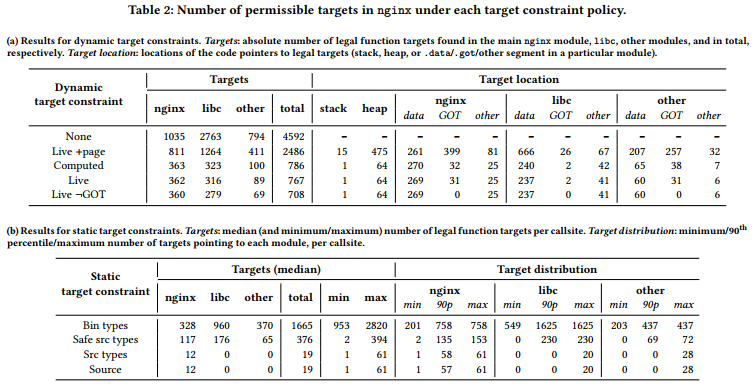
Evaluation
Bypass Context-Sensitive CFI
//in the function ngx_http_write_filter chain = c->send_chain(c, r->out, limit);
Bypass Code Pointer Integrity
//in the function ngx_http_get_indexed_variable v[index].get_handler(r, &r->variables[index], v[index].data);
[…] I find that Google CTF Quals take PICIF as a pwn chanllenge. Since this paper is also mentioned in The Dynamics of Innocent Flesh on the Bone: Code Reuse Ten Years Later, I decide to take simple note no this paper and take the pwn challenge to […]
LikeLike