Introduction
Write a post to log the necessary steps for Linux Kernel pwn challenges in CTF.
Read More »
Write a post to log the necessary steps for Linux Kernel pwn challenges in CTF.
Read More »
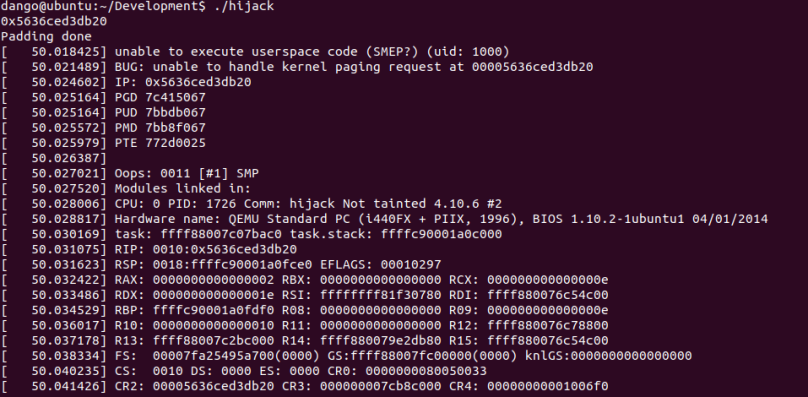
I’d like to talk about the ret2usr attack in Linux kernel exploitation and the corresponding Supervisor Mode Execution Prevention (SMEP). Rather than detailing the exploitation details in control flow hijacking, this post will explain what is ret2usr attack and what is the expected behaviour from SMEP.
Read More »

I will continue to talk about the exploitation of CVE-2017-7308. In this post, I will discuss the implementation details of buddy allocator and SLUB allocator in Linux-4.10.6. I will show how to put the victim object (struct packet_sock in this post) next adjacent to the vulnerable buffer (packet rv_ring buffer in previous post).
In [3], a general abstraction of Linux Kernel memory management is given as following picture. From the picture, we can find that two types of allocators (slab allocator and buddy allocator) are provided for Linux kernel functions. For both allocators, I will give some debugging info to give a straight view on how those objects are allocated and shaped in memory combined with some explanation on the source code.
Read More »

These days I think there is still necessity to write a tutorial series on Linux Kernel exploitation and hope to summarize the kernel exploitation techniques as following:
(1) Kernel Debugging
(2) Return-oriented-Programming in Kernel
(3) Kernel Mitigation: KASLR, SMEP, SMAP
(4) Kernel Space Memory Allocator: SLAB Allocator
In this post, I will introduce how to debug a Linux Kernel via CVE-2017-7308 [1], including setting up debugging environment, root cause analysis and exploit primitive analysis.
Read More »
The programme implements a simple logic in image processing. Since I started to learn GO binary just from CrossCTF, I spend a lot of time reversing the logic of the challenge.
Read More »

The virtual table is the key factor that achieves polymorphism in C++. This post will talk about the virtual table and its structure in C++. More particularly, I will introduce the virtual functions under Linux and Windows. All tests are done on 64-bit platform. 32-bit platform is a little bit different but the basic idea is similar.
Read More »

VTable reuse attack is a novel exploitation technique in recent academic work. I think it is time to give a short series of posts on VTable reuse attacks including academic papers, more details on VTable and VTable reuse attacks based on existing CVE.Read More »

This post will give a basic explanation of PHP (de)serialization and how such mechanism will be exploited in PHP Object Injection (POI).
Read More »

In my previous post, I introduce what is seccomp, how to set seccomp rule via seccomp_rule_add and how to bypass via ptrace. In this post, I am going to further introduce the seccomp filter, another way to set seccomp rule in the program. This post will also involve some kernel debugging for illustrating the internal of bpf filter.
Read More »