Introduction
This is my first pwn attempt on d8 engine. Write a blog to log the debugging process.
Vulnerability Analysis

According to the diff files given in the challenge, we can find it removes the length check of fill function of TypedArray. A simple script can trigger the crash

TypeArray Internal
To analyse the internal of the TypedArray, d8 already provides the debugging tool to view the the internal of TypedArray. More details are given in [1].
To test debugging, I take the following script as an example.

After running the script in gdb, we can get the following result:
Debugging info for arr1

Debugging info for arr2

After analyzing the TypeArray layout and some debugging test, I found that we can use the overwriting primitive of arr1 to overwrite the array base (in red block) of arr2 and the array size (in blue block) of arr2. After this step, we gain the arbitrary read/write primitive needed in exploitation.
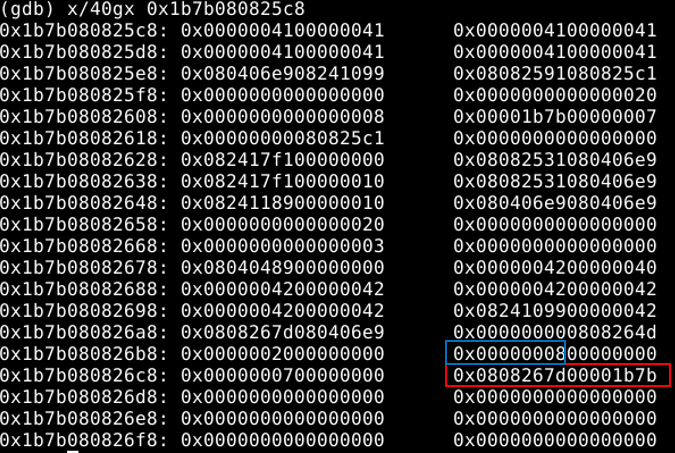
One thing to note is the data format of the base pointer of arr2.
Next step is to get a shell. My initial idea was to launch a shell with the magic gadget, but that proves to be wrong because this challenge does not provide the binary file of libc file. Therefore, the next option is to use the wasm code to create a RWX region in memory and overwrite the wasm code to shellcode.
After a long time struggling with the d8 debugging, the process to locate the address of RWX is straightforward. First, allocate the wasm object multiple times adjacent next to the leaking array. Then, view the memory map to locate the address of RWX region. Finally, search around the wasm object to locate the address of RWX region and get the regular rules.
Exploit
The final exploit is given on my github repo https://github.com/dangokyo/CTF/blob/master/CTF2020/p4ConfidentCFT/pwn/Chromatic/exploit.js
Reference
[1] https://syedfarazabrar.com/2019-12-13-starctf-oob-v8-indepth/